In today’s complex world, safeguarding your assets, people, and information goes beyond just digital defenses. Physical security is the foundational layer that protects everything else, and understanding its strengths and weaknesses is paramount. That’s where a comprehensive physical security assessment checklist template becomes an indispensable tool, helping organizations methodically review and enhance their protective measures against real-world threats.
Thinking about the vulnerabilities in your current setup might feel daunting, but a structured approach can turn that apprehension into actionable plans. A thorough assessment isn’t just about identifying problems; it is an opportunity to proactively strengthen your defenses, ensure compliance with industry standards, and ultimately provide a safer environment for everyone involved.
Whether you are a small business owner, a facility manager, or part of a larger enterprise, grasping the key elements of physical security is crucial. This guide will walk you through the essential components of a robust assessment, helping you build a resilient protective posture against a myriad of potential risks, from unauthorized access to environmental hazards.Understanding the Core Components of a Robust Physical Security Assessment
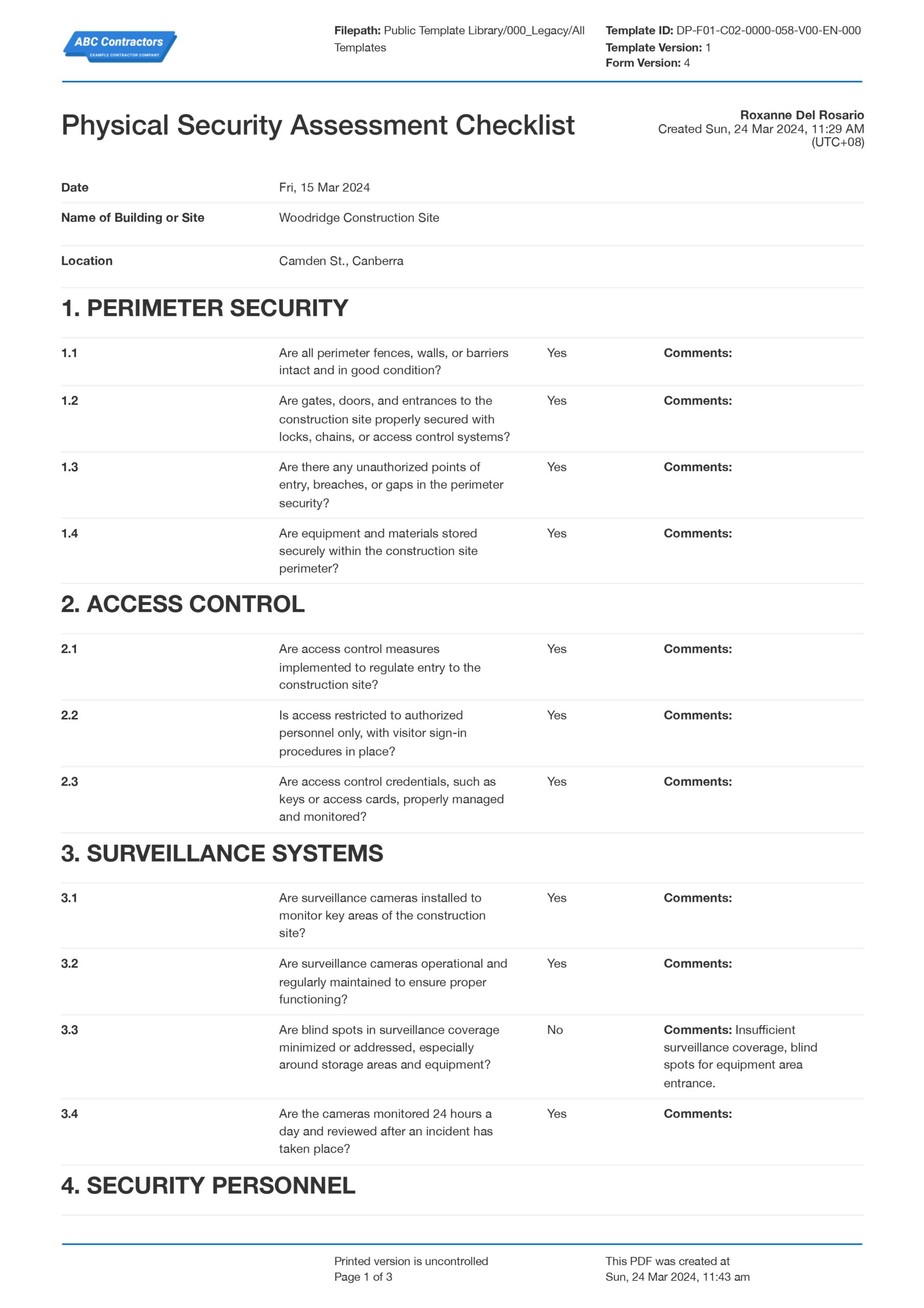
A truly effective physical security assessment dives deep into every layer of your protective environment, starting from the outermost boundaries and moving inwards. It’s about systematically examining infrastructure, technology, personnel, and procedures to identify potential weaknesses before they can be exploited. This holistic view ensures that no stone is left unturned in your quest for enhanced security.
The first line of defense often involves perimeter security. This section of the assessment scrutinizes external fences, gates, walls, and natural barriers. Are they robust enough to deter unauthorized entry? What about the lighting around the perimeter? Is it adequate to illuminate potential intruders and support surveillance systems? Assessing entry points like vehicle and pedestrian gates, their construction, and locking mechanisms is also critical.
Moving closer, the building exterior presents another crucial layer. This involves a detailed look at all access points such as doors, windows, loading docks, and emergency exits. Are all doors solid, properly secured with commercial-grade locks, and equipped with alarm contacts? Are windows shatter-resistant or protected by grates in vulnerable areas? This part of the assessment also evaluates the integrity of the building structure itself against forced entry.
Once inside, the focus shifts to internal zones and controlled areas. This includes server rooms, data centers, executive offices, laboratories, and any other locations housing sensitive information or valuable assets. Access control mechanisms, such as keycard systems, biometric scanners, or traditional key management protocols, are carefully examined. The assessment will determine if these controls are effectively limiting access to authorized personnel only.
Beyond physical structures, the role of security personnel and established procedures cannot be overstated. This involves evaluating the training, deployment, and effectiveness of security guards, if applicable. It also delves into visitor management protocols, incident response plans, emergency evacuation procedures, and the overall awareness of security policies among all staff. A robust plan is only as good as the people executing it.
Finally, technology integration forms a critical backbone of modern physical security. This segment assesses surveillance systems, including the placement, coverage, and quality of CCTV cameras. It also examines alarm systems, intrusion detection sensors, access control software, and communication systems used for security operations. Ensuring these systems are integrated, regularly maintained, and monitored effectively is paramount to their success.
Leveraging Your Checklist for Continuous Improvement
Once you’ve utilized your physical security assessment checklist template to identify potential vulnerabilities and areas for improvement, the work isn’t over. The true value of such a template lies in its ability to drive ongoing security enhancements. It’s not a one-time exercise but rather a dynamic process that evolves with your organization and the threat landscape.
The insights gained from the assessment should be meticulously documented and translated into an action plan. Prioritize the identified risks based on their potential impact and likelihood. For instance, a broken lock on a main entry door would likely take precedence over a minor lighting issue in a less frequented area. Assign responsibilities, set deadlines, and allocate resources to address each finding systematically.
Moreover, security is not static. New threats emerge, technology advances, and your operational needs change. Regularly scheduled assessments, perhaps annually or bi-annually, are crucial for maintaining a strong security posture. Each review allows you to measure progress, adapt to new challenges, and ensure your physical security measures remain effective and relevant against evolving risks.
Adopting a comprehensive, structured approach to evaluating your physical security is more than just a task; it is a commitment to safeguarding your environment. By systematically scrutinizing every aspect of your protective measures, you are actively building resilience against potential threats and ensuring the safety of your assets and the people within your premises.
Embracing a proactive mindset and regularly reviewing your security framework leads to peace of mind and a more secure operational environment. It’s about creating a robust, multi-layered defense that stands strong against the challenges of today and prepares effectively for those that may arise tomorrow.



