Navigating the complex world of cybersecurity can often feel like trying to solve a Rubik’s Cube blindfolded. With threats constantly evolving and regulations becoming stricter, ensuring your organization’s digital defenses are robust isn’t just a good idea; it’s an absolute necessity. But where do you even begin when you’re faced with the daunting task of assessing your entire security posture?
This is precisely where a structured approach becomes your best friend. Imagine having a clear roadmap that guides you through every critical aspect of your digital environment, helping you identify vulnerabilities before malicious actors do. That’s the power of a comprehensive cyber security audit checklist template, designed to simplify the intricate process of evaluating your security measures and ensuring peace of mind.
Understanding the Value of a Cyber Security Audit
A cyber security audit is essentially a systematic evaluation of your organization’s information system. It’s not just about looking for weaknesses; it’s about verifying that your security policies are effective, your controls are functioning as intended, and your data is adequately protected from unauthorized access, use, disclosure, disruption, modification, or destruction. Think of it as a thorough health check for your digital infrastructure.
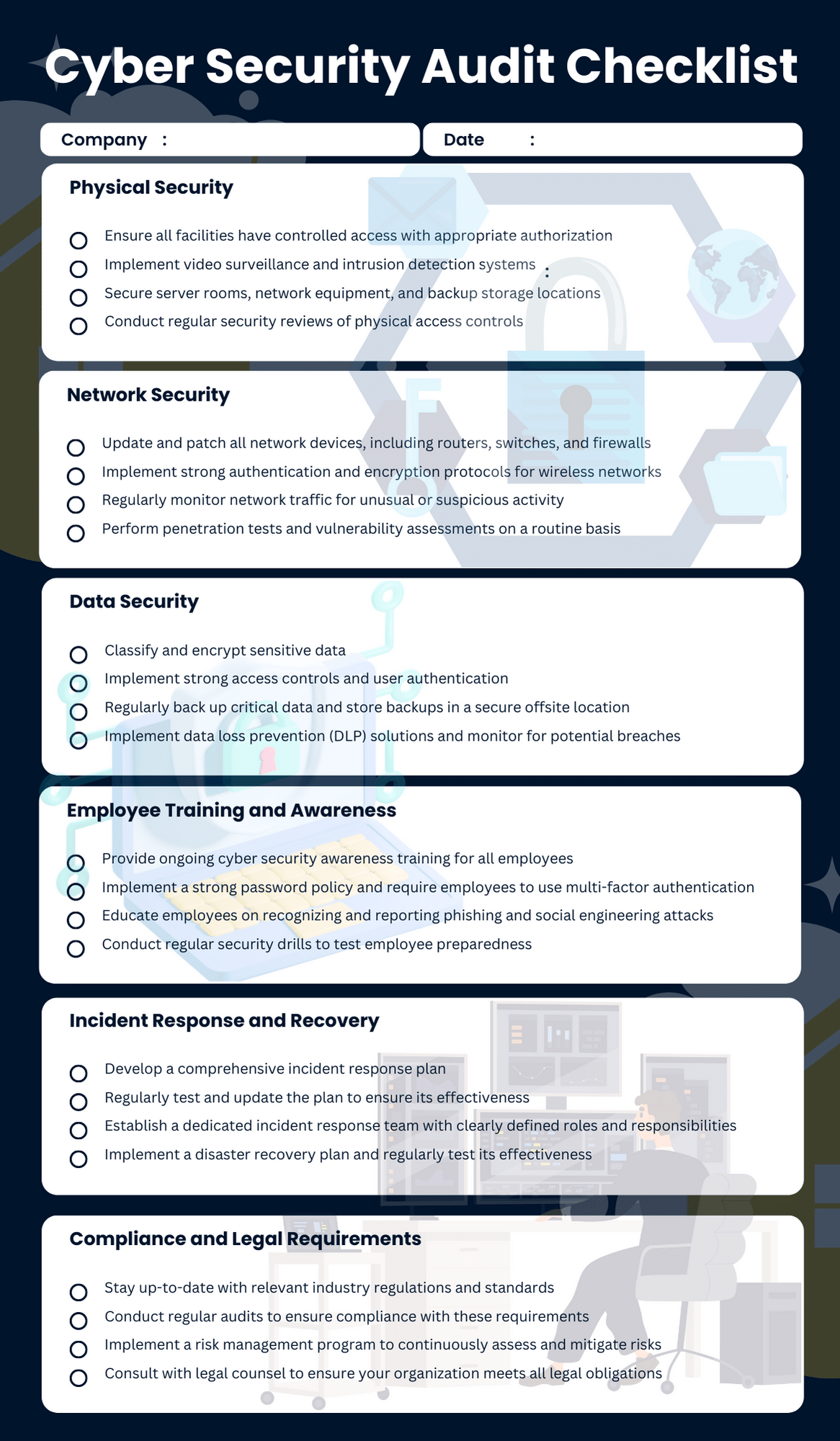
In today’s interconnected landscape, ignoring regular security audits is akin to leaving your front door unlocked in a bustling city. The consequences can range from devastating data breaches and significant financial losses to severe reputational damage and legal penalties. Regulatory compliance, such as GDPR, HIPAA, or CCPA, also often mandates these audits, making them a non-negotiable part of modern business operations. It’s about being proactive rather than reactive, catching potential issues before they escalate into full-blown crises.
Beyond mere compliance, an audit offers invaluable insights. It helps you understand where your strongest defenses lie and, more importantly, where your vulnerabilities are most pronounced. This knowledge empowers you to allocate resources effectively, prioritize improvements, and build a more resilient security framework. It’s an investment in the long-term stability and trustworthiness of your business.
Attempting to conduct an audit without a structured framework can quickly become an overwhelming and inefficient process. You might overlook critical areas, duplicate efforts, or struggle to track progress. This is where the systematic guidance of a robust cyber security audit checklist template truly shines, providing a step-by-step methodology to cover all essential aspects comprehensively. It ensures consistency and thoroughness, no matter who is performing the audit.
Key Areas a Comprehensive Audit Covers
A well-rounded audit should touch upon several crucial domains to provide a holistic view of your security posture.
- **Network Security:** Examining firewalls, intrusion detection systems, network segmentation, and wireless security.
- **Application Security:** Assessing web applications, APIs, and custom software for vulnerabilities like SQL injection or cross-site scripting.
- **Data Security:** Reviewing data encryption, access controls, data loss prevention (DLP) measures, and data backup/recovery protocols.
- **Identity and Access Management (IAM):** Checking user authentication methods, role-based access controls, and privileged access management.
- **Physical Security:** Evaluating controls around server rooms, data centers, and employee workstations to prevent unauthorized physical access.
- **Policy and Procedure Review:** Ensuring that security policies are current, clearly communicated, and regularly enforced among staff.
- **Incident Response Plan:** Testing the effectiveness of your incident response procedures, from detection and containment to eradication and recovery.
- **Vendor and Third-Party Risk Management:** Assessing the security practices of your suppliers and service providers who have access to your data or systems.
Crafting Your Effective Cyber Security Audit Checklist Template
Building an effective cyber security audit checklist template doesn’t mean starting from scratch every time. Instead, it involves leveraging industry best practices and tailoring them to your unique organizational context. Your template should be a living document, evolving as your technology stack changes and as new threats emerge. The goal isn’t just to check boxes, but to foster a culture of continuous security improvement.
Begin by segmenting your audit into logical sections, much like the key areas we discussed earlier. Within each section, break down the tasks into specific, actionable items. For instance, under "Network Security," you might have items like "Verify firewall rules are documented and reviewed quarterly" or "Ensure all network devices have strong, unique passwords and multi-factor authentication where applicable." Specificity is key to avoiding ambiguity and ensuring thoroughness.
Leverage existing frameworks like NIST, ISO 27001, or CIS Controls. These provide a solid foundation and can guide the inclusion of essential controls and best practices into your custom checklist. While these frameworks can be extensive, you can extract the most relevant sections for your organization’s size, industry, and risk profile. Remember, your template should be robust enough to catch significant vulnerabilities but also practical enough to be implemented without overwhelming your team.
Once you have your core cyber security audit checklist template, the real work begins. Schedule regular audits, assigning clear responsibilities for each item. Document all findings, including both compliant areas and identified deficiencies. For every deficiency, outline a clear remediation plan with assigned owners and realistic deadlines. The audit process isn’t complete until these remediation actions are tracked and verified. Regular review and updates to your template itself will ensure it remains relevant and effective in an ever-changing threat landscape, providing continuous assurance for your digital assets.
A structured audit process provides clarity and direction, turning a potentially overwhelming task into a manageable and empowering exercise. It ensures that your organization not only meets regulatory obligations but also actively fortifies its defenses against an increasingly sophisticated array of cyber threats. By consistently applying a thorough checklist, you’re not just securing data; you’re building trust and resilience into the very fabric of your operations.